Introduction
In this post, we will explore new features in both tpm report and tpm ask in v7.1.0. Both commands will continue to evolve and grow over time. In this release we have added new information to the `tpm report` output when requested and new actions, arguments and keys for `tpm ask`.
A Bit of Review: tpm report
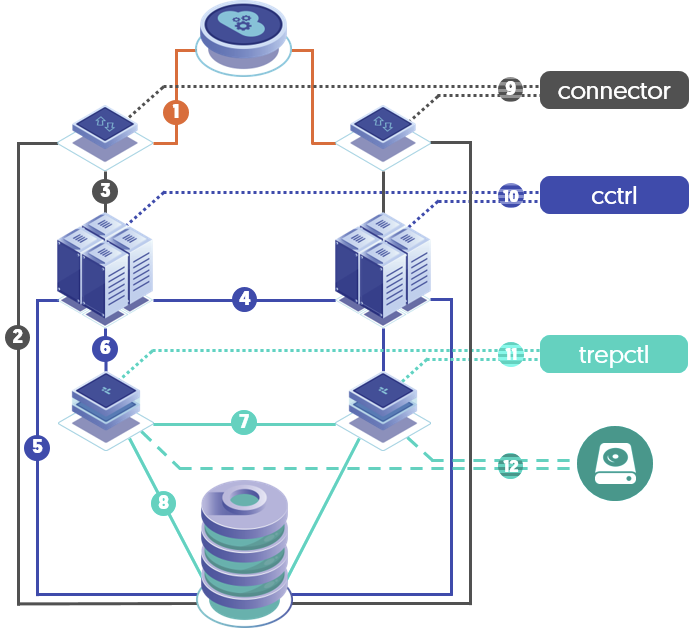
The default Security report reflects the various cluster communications channels. Currently, there are 18 channels reported on. To get a list of the channels, run `tpm report --list` or `tpm report -l`:
| Channel (Protocol) | Description | |
|---|---|---|
| 1 | Application to Connector (mysql) | Communications from the client application to the Connector port |
| 2 | Connector to Database (mysql) | Communications from the Connector to the Database port |
| 3 | Connector to Manager (proprietary (routerGateway)) | Communications from the Connector to the Manager |
| 4 | Manager to Manager (rmi/jmx, jgroups) | Communications from Manager to Manager |
| 5 | Manager to Database (mysql) | Communications from Manager to Database |
| 6 | Manager to Replicator (rmi/jmx) | Communications from Manager to Replicator |
| 7 | Replicator to Replicator (thl) | Communications from Replicator to Replicator |
| 8 | Replicator to Database (mysql) | Communications from Replicator to Database |
| 9 | connector Command to the Connector (rmi/jmx) | Communications from the connector cli command to the to local Connector process |
| 10 | cctrl Command to the Manager (rmi/jmx) | Communications from the cctrl cli command to the to Manager process |
| 11 | trepctl Command to the Replicator (rmi/jmx) | Communications from the trepctl cli command to the to Replicator process |
| 12 | Replicator On Disk THL (proprietary (thl encryption)) | THL files on disk are encrypted |
| 13 | Replicator Tanuki Wrapper Listener (JVM Ping) | Tanuki Wrapper JVM Liveness Checks |
| 14 | Manager Tanuki Wrapper Listener (JVM Ping) | Tanuki Wrapper JVM Liveness Checks |
| 15 | Connector Tanuki Wrapper Listener (JVM Ping) | Tanuki Wrapper JVM Liveness Checks |
| 16 | Replicator Internal RMI Communications (rmi/jmx) | Replicator-specific Internal-use TCP high ports for RMI |
| 17 | Manager Internal RMI Communications (rmi/jmx) | Manager-specific Internal-use TCP high ports for RMI |
| 18 | SSL-Specific `tpm` Options for the API (http, https) | Options used by tpm to enable or disable the API for each component |
Displaying All Reports - Review
To show all reports:
shell> tpm report
To show all reports with any available “extra” (-x) information:
shell> tpm report -x
To show just channel 1:
shell> tpm report -report 1
New `tpm report` Argument: --ports
To display the port information for each channel in a report, specify it using --ports.
shell> tpm report --ports -report 6
TUNGSTEN SECURITY REPORT (via CLI) as of Thu Jul 27 18:25:34 UTC 2023
---------------------------------------------------------------------------
>> Comm Channel 6: Manager to Replicator <<
---------------------------------------------------------------------------
=> CHANNEL INFORMATION (via CLI):
Manager-To-Replicator RMI/JMX SSL is Enabled [Ports 10000, 10001]
=> TPM OPTIONS:
disable-security-controls = false
enable-rmi-ssl = true
enable-rmi-authentication = true
=> SECURITY INFO:
security.keystore.alias=tls, java-tls-entry-alias
security.keystore.location=/opt/continuent/share/tungsten_keystore.jks, java-keystore-path
security.rmi.authentication.username=tungsten, rmi-user
security.rmi.authentication=true, enable-rmi-authentication
security.rmi.encryption=true, enable-rmi-ssl
security.rmi.tungsten.authenticationRealm=true
security.truststore.location=/opt/continuent/share/tungsten_truststore.ts, java-truststore-path
New `tpm report` Security Content
Each channel will now show the related security.properties keys, values and tpm options:
shell> tpm report --ports --report 4
---------------------------------------------------------------------------
>> Comm Channel 4: Manager to Manager <<
---------------------------------------------------------------------------
=> CHANNEL INFORMATION (via CLI):
Manager-To-Manager RMI/JMX SSL is Enabled [Port 9997]
Manager-To-Manager JGroups SSL is Enabled [Port 7800]
=> TPM OPTIONS:
disable-security-controls = false
enable-jgroups-ssl = true
enable-rmi-ssl = true
enable-rmi-authentication = true
=> SECURITY INFO:
manager.jgroups.use.ssl=true, manager-jgroups-use-ssl
security.keystore.alias=tls, java-tls-entry-alias
security.keystore.location=/opt/continuent/share/tungsten_keystore.jks, java-keystore-path
security.rmi.authentication.username=tungsten, rmi-user
security.rmi.authentication=true, enable-rmi-authentication
security.rmi.encryption=true, enable-rmi-ssl
security.rmi.tungsten.authenticationRealm=true
security.truststore.location=/opt/continuent/share/tungsten_truststore.ts, java-truststore-path
New Action, Arguments and Keys for tpm ask
New Action: tpm ask find {searchString}
There is one new action: tpm ask find {searchString} to help you locate the specific key you are looking for:
shell> tpm ask find cert
certlocations
certs
certtpm
New Arguments: --file, --long and –quick
| [--file {file}] | Used with key summary, output to {file} instead of the screen (aliases: -o and -F) |
| [--quick] | Used with key summary, skip the long operations (alias: -k) |
| [--long] | Include the variable (key) name in the output (alias: -l) |
This is an example of the difference using --long to add the called key name to the output:
shell> tpm ask dsrole
replica
shell> tpm ask dsrole -l
dsrole = replica
Here is the short summary output by using --quick to limit the output to the fast operations, and also using --file to store the output to disk:
shell> tpm ask summary --quick
{
"composite" : null,
"dsNodes" : [
"db1-demo.continuent.com",
"db2-demo.continuent.com",
"db3-demo.continuent.com",
"db4-demo.continuent.com",
"db5-demo.continuent.com"
],
"home_directory" : "/opt/continuent",
"installMode" : "ini",
"isCAA" : 0,
"isCAP" : 0,
"isClustering" : 1,
"isComposite" : 0,
"isConnector" : 1,
"isConnectorHost" : 1,
"isEnabled" : {
"replicator" : 1,
"connector" : 1,
"manager" : 1
},
"isINI" : 1,
"isInstalled" : 1,
"isManager" : 1,
"isReplicator" : 1,
"isRunning" : {
"thl" : 0,
"cctrl" : 0,
"startall" : 0,
"tpm" : 0,
"manager" : 1,
"trepctl" : 0,
"replicator" : 1,
"connector" : 1,
"stopall" : 0
},
"isSTD" : 1,
"isStaging" : 0,
"isWitness" : 0,
"scriptPath" : "/opt/continuent/releases/tungsten-clustering-7.1.0-138_pid22248/tools/perl-tpm",
"serviceByNode" : {
"db1-demo.continuent.com" : "ddg",
"db2-demo.continuent.com" : "ddg",
"db5-demo.continuent.com" : "ddg",
"db4-demo.continuent.com" : "ddg",
"db3-demo.continuent.com" : "ddg"
},
"services" : {
"ddg" : "local"
},
"tdir" : "/opt/continuent/releases/tungsten-clustering-7.1.0-138_pid22248",
"tpmmode" : "installed",
"version" : "7.1.0-138",
"versions" : {
"software" : {
"version" : "7.1.0.138",
"label" : "7.1.0-138",
"major" : "7"
},
"installed" : {
"version" : "7.1.0.138",
"label" : "7.1.0-138",
"major" : "7"
}
}
}
shell> tpm ask summary --quick --file summary.txt
Writing content to summary.txt...SUCCESS
New Keys: certlocations, certs, certtpm, clusterinfo, ro and ver
Finally, tpm ask has 6 new keys you can call for:
certlocations |
Display the value and tpm option for each key found in the security.properties file |
certs |
Display the running security file information as json. Similar to `tpm cert info all --running` |
certtpm |
Display the tpm option for the related security.properties key, if one exists |
clusterinfo |
Display the datasource role and state, the replicator progress and the ddgID if available for the node as json |
ro |
Display 1 for if the database server is set to Read-Only, and 0 if the database is set to Read-Write based on the output of `mysql> select @@read_only;` |
ver |
Display the current software version (same as `tpm query version`) |
shell> tpm ask certlocations
{
"connector.api.security.keystore.location" : {
"val" : "/opt/continuent/share/tungsten_keystore.jks",
"tpm" : "java-keystore-path"
},
"connector.api.security.truststore.location" : {
"val" : "/opt/continuent/share/tungsten_truststore.ts",
"tpm" : "java-truststore-path"
},
"connector.security.keystore.location" : {
"val" : "/opt/continuent/share/tungsten_connector_keystore.jks",
"tpm" : "java-connector-keystore-path"
},
"connector.security.truststore.location" : {
"val" : "/opt/continuent/share/tungsten_connector_truststore.ts",
"tpm" : "java-connector-truststore-path"
},
"manager.api.security.keystore.location" : {
"val" : "/opt/continuent/share/tungsten_keystore.jks",
"tpm" : "java-keystore-path"
},
"manager.api.security.truststore.location" : {
"val" : "/opt/continuent/share/tungsten_truststore.ts",
"tpm" : "java-truststore-path"
},
"replicator.api.security.keystore.location" : {
"val" : "/opt/continuent/share/tungsten_keystore.jks",
"tpm" : "java-keystore-path"
},
"replicator.api.security.truststore.location" : {
"val" : "/opt/continuent/share/tungsten_truststore.ts",
"tpm" : "java-truststore-path"
},
"security.access_file.location" : {
"val" : "/opt/continuent/share/jmxremote.access",
"tpm" : "java-jmxremote-access-path"
},
"security.keystore.location" : {
"val" : "/opt/continuent/share/tungsten_keystore.jks",
"tpm" : "java-keystore-path"
},
"security.password_file.location" : {
"val" : "/opt/continuent/share/passwords.store",
"tpm" : "java-passwordstore-path"
},
"security.thl.keystore.location" : {
"val" : "/opt/continuent/share/tungsten_thl_keystore.jks",
"tpm" : "java-thl-keystore-path"
},
"security.thl.truststore.location" : {
"val" : "/opt/continuent/share/tungsten_thl_truststore.ts",
"tpm" : "java-thl-truststore-path"
},
"security.truststore.location" : {
"val" : "/opt/continuent/share/tungsten_truststore.ts",
"tpm" : "java-truststore-path"
}
}
shell> tpm ask certs
{
"java-connector-keystore-path" : {
"file" : "/opt/continuent/share/tungsten_connector_keystore.jks",
"aliases" : {
"mysql" : {
"expires" : "Sun Jul 17 16:50:13 UTC 2033",
"sha256" : "8A:0C:BD:D8:78:0C:4B:B4:85:DE:31:D2:BF:F5:4C:8E:6F:AC:A2:50:2A:8D:58:C8:73:7D:91:74:59:F8:3E:8E",
"sha1" : "1A:4C:EB:41:A1:8D:47:6D:45:05:90:50:16:C8:C0:4B:F0:95:DF:1B"
}
}
},
"java-connector-truststore-path" : {
"file" : "/opt/continuent/share/tungsten_connector_truststore.ts",
"aliases" : {
"mysql" : {
"expires" : "Sun Jul 17 16:50:12 UTC 2033",
"sha256" : "28:9F:E6:78:19:E0:D3:CD:A3:97:5F:8B:30:AB:6C:E3:EA:AB:34:55:30:72:9D:27:2B:A9:F8:B5:7F:06:92:2C",
"sha1" : "9E:9B:03:51:EB:0E:9A:9D:CB:57:47:8E:19:98:37:8D:07:7B:ED:1F"
}
}
},
"java-jmxremote-access-path" : {
"file" : "/opt/continuent/share/jmxremote.access"
},
"java-keystore-path" : {
"file" : "/opt/continuent/share/tungsten_keystore.jks",
"aliases" : {
"mysql" : {
"expires" : "Sun Jul 17 16:50:13 UTC 2033",
"sha256" : "8A:0C:BD:D8:78:0C:4B:B4:85:DE:31:D2:BF:F5:4C:8E:6F:AC:A2:50:2A:8D:58:C8:73:7D:91:74:59:F8:3E:8E",
"sha1" : "1A:4C:EB:41:A1:8D:47:6D:45:05:90:50:16:C8:C0:4B:F0:95:DF:1B"
},
"tls" : {
"expires" : "Fri Jul 22 17:26:03 UTC 2033",
"sha256" : "62:11:99:BC:1A:68:01:4F:D8:D2:59:F4:EA:64:CB:1E:41:9C:EC:E1:9B:A9:19:92:A6:B2:A2:39:3F:59:F1:00",
"sha1" : "22:D5:76:5A:5C:5D:E7:4A:A7:72:7A:E5:5F:CC:BB:63:EB:87:B6:E6"
}
}
},
"java-passwordstore-path" : {
"file" : "/opt/continuent/share/passwords.store"
},
"java-thl-keystore-path" : {
"file" : "/opt/continuent/share/tungsten_thl_keystore.jks",
"aliases" : {
"tls" : {
"expires" : "Fri Jul 22 17:26:03 UTC 2033",
"sha256" : "62:11:99:BC:1A:68:01:4F:D8:D2:59:F4:EA:64:CB:1E:41:9C:EC:E1:9B:A9:19:92:A6:B2:A2:39:3F:59:F1:00",
"sha1" : "22:D5:76:5A:5C:5D:E7:4A:A7:72:7A:E5:5F:CC:BB:63:EB:87:B6:E6"
}
}
},
"java-thl-truststore-path" : {
"file" : "/opt/continuent/share/tungsten_thl_truststore.ts",
"aliases" : {
"tls" : {
"expires" : "Fri Jul 22 17:26:03 UTC 2033",
"sha256" : "62:11:99:BC:1A:68:01:4F:D8:D2:59:F4:EA:64:CB:1E:41:9C:EC:E1:9B:A9:19:92:A6:B2:A2:39:3F:59:F1:00",
"sha1" : "22:D5:76:5A:5C:5D:E7:4A:A7:72:7A:E5:5F:CC:BB:63:EB:87:B6:E6"
}
}
},
"java-truststore-path" : {
"file" : "/opt/continuent/share/tungsten_truststore.ts",
"aliases" : {
"mysql" : {
"expires" : "Sun Jul 17 16:50:12 UTC 2033",
"sha256" : "28:9F:E6:78:19:E0:D3:CD:A3:97:5F:8B:30:AB:6C:E3:EA:AB:34:55:30:72:9D:27:2B:A9:F8:B5:7F:06:92:2C",
"sha1" : "9E:9B:03:51:EB:0E:9A:9D:CB:57:47:8E:19:98:37:8D:07:7B:ED:1F"
},
"tls" : {
"expires" : "Fri Jul 22 17:26:03 UTC 2033",
"sha256" : "62:11:99:BC:1A:68:01:4F:D8:D2:59:F4:EA:64:CB:1E:41:9C:EC:E1:9B:A9:19:92:A6:B2:A2:39:3F:59:F1:00",
"sha1" : "22:D5:76:5A:5C:5D:E7:4A:A7:72:7A:E5:5F:CC:BB:63:EB:87:B6:E6"
}
}
}
}
shell> tpm ask certtpm
{
"connector.api.security.authentication.checker.class" : "com.continuent.tungsten.api.server.security.authenticationchecker",
"connector.api.security.authentication" : "conn-rest-api-authentication",
"connector.api.security.keystore.alias" : "java-tls-entry-alias",
"connector.api.security.keystore.location" : "java-keystore-path",
"connector.api.security.keystore.password" : "java-keystore-password",
"connector.api.security.truststore.location" : "java-truststore-path",
"connector.api.security.truststore.password" : "java-truststore-password",
"connector.security.keystore.location" : "java-connector-keystore-path",
"connector.security.keystore.password" : "java-connector-keystore-password",
"connector.security.truststore.location" : "java-connector-truststore-path",
"connector.security.truststore.password" : "java-connector-truststore-password",
"connector.security.use.ssl" : "enable-connector-client-ssl",
"manager.api.security.authentication.checker.class" : "com.continuent.tungsten.api.server.security.authenticationchecker",
"manager.api.security.authentication" : "mgr-rest-api-authentication",
"manager.api.security.keystore.alias" : "java-tls-entry-alias",
"manager.api.security.keystore.location" : "java-keystore-path",
"manager.api.security.keystore.password" : "java-keystore-password",
"manager.api.security.truststore.location" : "java-truststore-path",
"manager.api.security.truststore.password" : "java-truststore-password",
"manager.jgroups.use.ssl" : "manager-jgroups-use-ssl",
"replicator.api.security.authentication.checker.class" : "com.continuent.tungsten.api.server.security.authenticationchecker",
"replicator.api.security.authentication" : "repl-rest-api-authentication",
"replicator.api.security.keystore.alias" : "java-tls-entry-alias",
"replicator.api.security.keystore.location" : "java-keystore-path",
"replicator.api.security.keystore.password" : "java-keystore-password",
"replicator.api.security.truststore.location" : "java-truststore-path",
"replicator.api.security.truststore.password" : "java-truststore-password",
"security.access_file.location" : "java-jmxremote-access-path",
"security.dir" : "security-directory",
"security.enabled.cipher.suites" : "tls-enabled-cipher-suites",
"security.enabled.protocols" : "tls-enabled-protocols",
"security.keystore.alias" : "java-tls-entry-alias",
"security.keystore.location" : "java-keystore-path",
"security.keystore.password" : "java-keystore-password",
"security.password_file.location" : "java-passwordstore-path",
"security.randomWaitOnFailedLogin.increment.step " : " 100",
"security.randomWaitOnFailedLogin.max " : " 1000",
"security.randomWaitOnFailedLogin.min " : " 500",
"security.rmi.authentication.username" : "rmi-user",
"security.rmi.authentication" : "enable-rmi-authentication",
"security.rmi.encryption" : "enable-rmi-ssl",
"security.rmi.tungsten.authenticationRealm.encrypted.password" : "true",
"security.rmi.tungsten.authenticationRealm" : "true",
"security.thl.keystore.alias" : "java-tls-entry-alias",
"security.thl.keystore.location" : "java-thl-keystore-path",
"security.thl.keystore.password" : "java-keystore-password",
"security.thl.truststore.location" : "java-thl-truststore-path",
"security.thl.truststore.password" : "java-truststore-password",
"security.truststore.location" : "java-truststore-path",
"security.truststore.password" : "java-truststore-password"
}
shell> tpm ask clusterinfo
{
"db1-demo.continuent.com" : {
"ddgid" : "100",
"progress" : "7",
"role" : "replica",
"state" : "ONLINE"
},
"db2-demo.continuent.com" : {
"ddgid" : "100",
"progress" : "7",
"role" : "primary",
"state" : "ONLINE"
},
"db3-demo.continuent.com" : {
"ddgid" : "200",
"progress" : "7",
"role" : "replica",
"state" : "ONLINE"
},
"db4-demo.continuent.com" : {
"ddgid" : "200",
"progress" : "7",
"role" : "replica",
"state" : "ONLINE"
}
}
shell> tpm ask ro
1
shell> tpm ask ver
7.1.0-138
Wrap-Up
The tpm report and tpm ask commands continue to evolve and grow over time. This latest version is Continuent’s way of providing as much transparency about Tungsten Cluster security as possible.
In this post we examined the new `tpm report --ports` argument, along with various new tpm ask arguments (--file, --quick, --long), keys (certlocations, certs, certtpm, clusterinfo, ro, ver) and one action (find).


Comments
Add new comment